Running a web server on the Internet requires knowledge about many security issues. FotoWeb has been designed to fit into the security model of Windows. The concepts for managing security in FotoWeb should therefore already be known by those familiar with Windows’ security.
FotoWeb uses the Process Account configured in the Operations Center to run the system. The account password is stored in encrypted form in the FotoWeb configuration files. If you change the account passwords in Windows, you must always remember to update the password in the Operations Center and IIS as well. If you try to start FotoWeb with a wrong password, the account may be locked out by Windows, and FotoWeb will not work correctly until you enter the correct password and unlock the account using the user administration tools in Windows.
Even if FotoWeb has been designed to be secure, most hackers will attack vulnerabilities in widely known network hardware and software. You should always consult someone with good knowledge in these areas before placing your server on the Internet.
The network topologies shown in this chapter are examples of different configurations, each with different tradeoffs in security, functionality and performance. Which one you choose to implement, or if you choose to implement a different topology, depends on both your need of security, which functionality that is important for you and your budget. This chapter is included in this document for informational purposes only. Always consult someone with first-hand knowledge of security before choosing or implementing any of these suggestions. Other solutions not mentioned here may also prove better in your scenario.
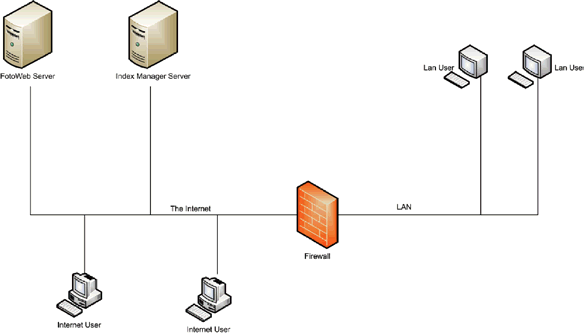
Placing your server directly on the Internet is an affordable solution. It ensures your internal LAN is completely protected by a firewall. It is also an optimal solution when it comes to performance, as users have direct access to the FotoWeb server.

With this topology it is a difficult, or even impossible, task to secure the operating system from hacker attacks, and is not recommended unless performance or budget is a key issue.
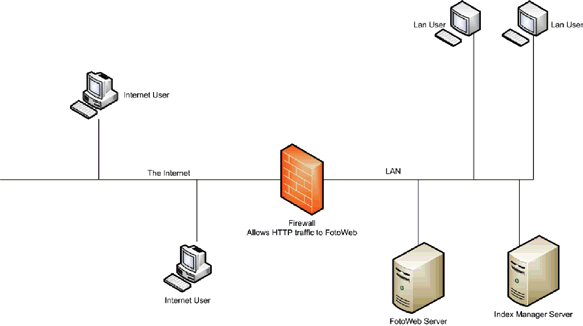
Another affordable option is to place the FotoWeb server on your internal LAN, which is protected by a firewall or a packet filtering router. The firewall must be configured to allow traffic on the Http protocol to pass through to the FotoWeb server.
In addition to giving your server basic protection behind a firewall, it allows your internal users to work directly with the archive using the FotoStation or FotoWeb clients. It is easy to manage your servers, and your internal users have optimal performance when accessing the archives.
However, in the case where a hacker is able to compromise your web server, your entire network will be vulnerable to an attack.
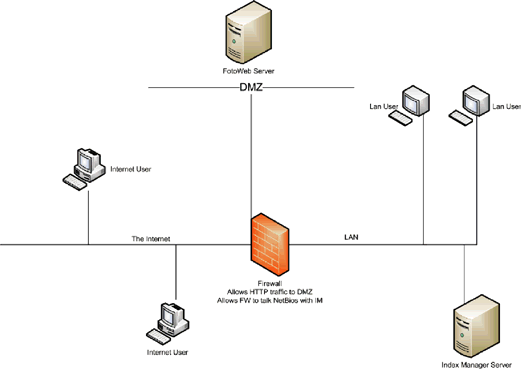
More advanced firewalls can be configured with one or more ‘Demilitarized Zones’. A DMZ is a separate network in which you can place servers that will be available from the Internet. In this configuration, internal users will be able to work with the archive using FotoStation with full speed and functionality. The firewall needs to be configured so that the FotoWeb server can access the share containing the documents on the Index Manager server and to communicate with the Index Manager server over IP (port 7000 by default). FotoWeb accesses the document folders using standard Windows shares (using the NETBIOS protocol).
This solution is not optimal from a performance point of view. FotoWeb needs to access all the files through the firewall, which can have a significant negative effect on the performance. It may also be possible for a hacker to exploit this tunnel in the firewall to attack the internal LAN after compromising the web server.
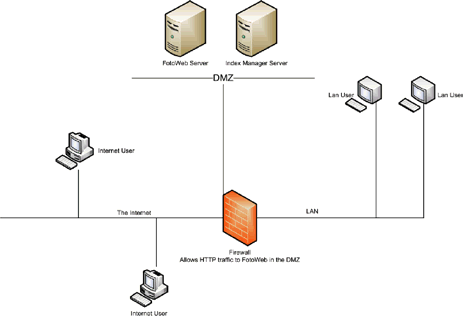
Using a firewall with DMZ capability, you can place both the Index Manager and FotoWeb servers in the DMZ. The firewall allows traffic to the DMZ, but not to the internal LAN. If a user is able to compromise your web server, it is still impossible to attack the internal LAN.
This solution has an effect on the performance of the internal users. If they are using FotoStation to manage the archive, all access has to pass through the firewall, which is slower than when the server is available on the same network. However, the security gained by this solution may justify the performance degradation.

If you have a large production workflow on your servers, it may not be a good option to access the document archive through the firewall as in the previous example. In this case, you may benefit from running duplicate servers. One set of servers is reserved for access from the internet, while another set is private to your internal LAN. This introduces complexity in duplicating data between the systems, but ensures maximum performance and security. However, it introduces the costs of licensing the software for more servers.
If you have a production workflow on your internal system and only provide a subset of the documents on the external archive (e.g. the result of the production), this solution is ideal.
A one-way mirror is also quite easily implemented. However, if changes are made in both systems this solution may present challenges that are either very difficult or impossible to implement.