When Operations Center is installed, it will install a self-signed certificate for secure communications and bind it to port 7001. If you later change the port, it will automatically bind the certificate to the new port. Hence, Operations Center and all FotoWare server and client applications have built-in support for secure HTTP communications.
Note: When accessing the Operations Center on a secure connection with a self-signed certificate (by typing in https://servername:7001 in your web browser's address field) your browser will display a warning that the certificate is not trusted. That's because it is self-signed and not issued by a trusted certificate provider. However, you can safely proceed to configure the Operations Center knowing that all traffic is transferred on a secure connection.
If you want to use a site certificate from a trusted source, you can do so by purchasing one from a trusted supplier.
After your certificate has been delivered it is typically stored on your computer. You will then have to bind the certificate to port 7001 on your server. But because FotoWare may already have created a self-signed certificate and bound it to port 7001, you may have to ubind that certificate from the port and then bind the new, purchased, trusted certificate to port 7001.
The procedure for accomplishing this is described below.
Checking whether a self-signed certificate is tied to port 7001
Important: Before proceeding, make sure you stop the Operations Center service on the server.
Open the command prompt on your server. (Start | Run cmd) Then proceed as outlined below based on which version of Windows Server you are using.
Type in netsh http show sslcert.
Type httpcfg query ssl
This will list any SSL certificate bindings. If you find a entry named IP:Port 0.0.0.0:7001 that means a certificate (most likely the FotoWare self-signed one) is bound to port 7001. You will have to delete this binding before you can bind your purchased, trusted certificate to port 7001.
Note: If no bindings are listed, proceed to Binding your trusted certificate to port 7001 below.
Deleting the self-signed certificate's binding to port 7001
If a certificate is already bound to port 7001, that would be the FotoWare self-signed certificate. You will have to remove this binding before you can bind to another certificate:
On the command prompt, type in the following to delete the certificate's binding to port 7001:
netsh http delete sslcert ipport=0.0.0.0:7001
In Windows 2003, type httpcfg delete ssl -i 0.0.0.0:7001
Binding your trusted certificate to port 7001
Before you can bind your new certificate to the port, you will need to locate its thumbprint. You can do so in Microsoft Management Console. To start it, open the Start menu and click Run, then type in MMC.
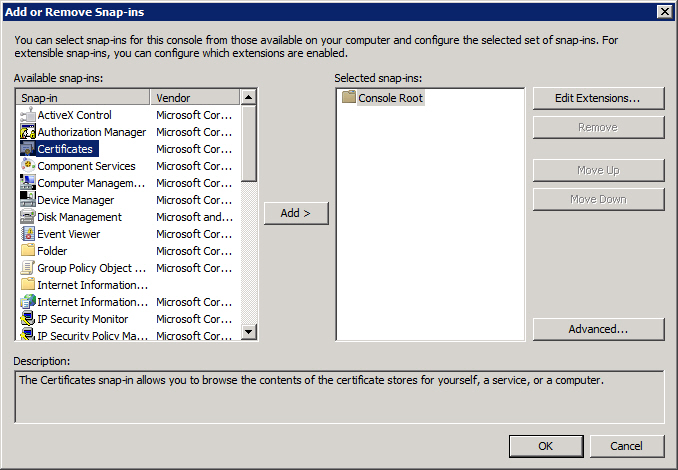
Now, open the File menu and choose Add/Remove Snap-in:

Select Certificates and click on the Add button.
Select Computer Account and click on Next.
Choose Local computer (assuming the signed certificate was stored on the local computer) and click on Finish.
Click on OK to close the Snap-In manager
Now expand the Certificates (Local Computer) node, then the Personal node, and then click on the Certificates node:
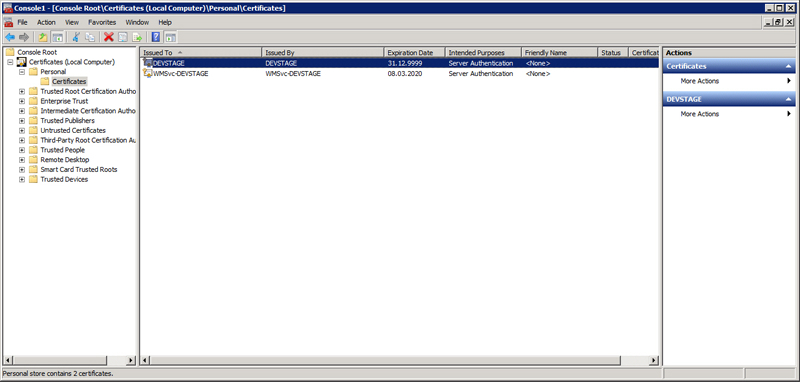
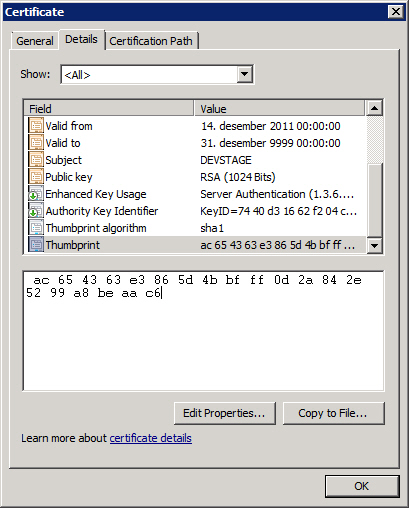
Double-click on the signed certificate to open its properties and click on the Details tab.
Then scroll down to the Thumbprint property and copy the thumbprint hash to the clipboard. You will need this thumbprint to create a port binding in the next step, but you will have to remove the spaces between the values. Hence, it may be a good idea to paste the string into Notepad, for example to remove the spaces.
Now, open the command prompt and type in the command below. (Note how the syntax is different in Windows server 2008 / 2003.)
netsh http add sslcert ipport=0.0.0.0:7001 certhash=0000000000003ed9cd0c315bbb6dc1c08da5e6 appid={00112233-4455-6677-8899-AABBCCDDEEFF}
Replace the certhash variable (in green) with the thumbprint of the certificate you are installing. Remember to remove the spaces between the thumbprint's values as described above, if you have not already done so. The port number for the binding is emphasized in red text above, while the appid is in blue type. The appid parameter is a GUID that can be used to identify the owning application. You will have to generate a GUID (Globally Unique Identifier) for your application - there are many utilities available on the web that will let you do this - for example http://www.guidgenerator.com/
httpcfg set ssl -i 0.0.0.0:7001 -h 0000000000003ed9cd0c315bbb6dc1c08da5e6
Replace the certhash variable (in green) with the thumbprint of the certificate you are installing. Remember to remove the spaces between the thumbprint's values as described above, if you have not already done so. The port number for the binding is emphasized in red text above.
Now that the certificate binding has been configured, you may want to require clients to connect securely to the server using SSL.